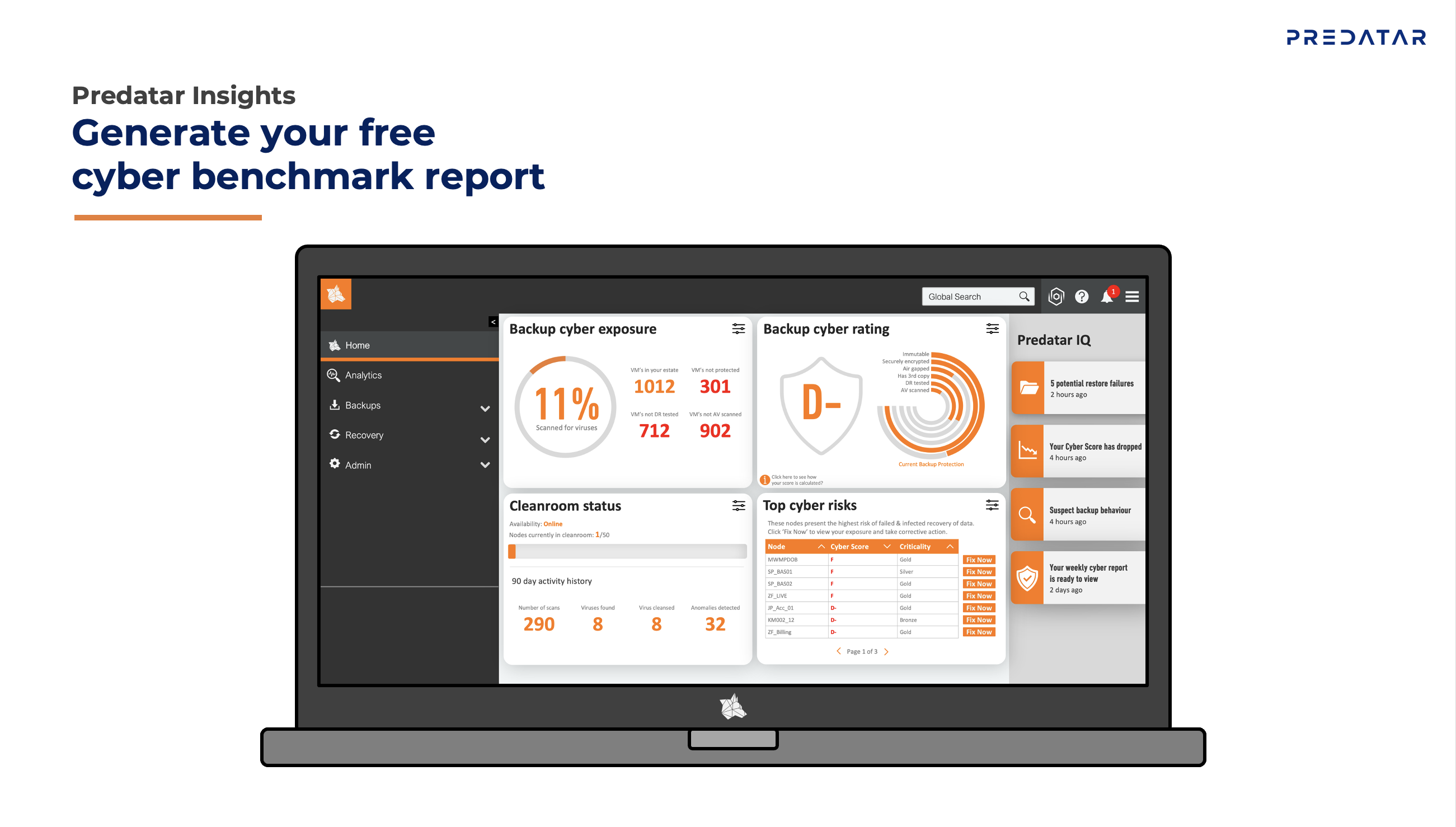
IBM Spectrum Protect Server 8.1.14.000
The IBM Spectrum Protect 8.1.14.000 server could allow an attacker to bypass security restrictions caused by improper enforcement of access controls.
By logging in, an attacker could exploit this vulnerability to bypass security and gain unauthorized administrator or node access to the vulnerable server.
Attack target: Gain privileges
Existing attack scenarios: Not known
Affected: Spectrum Protect Server up to 8.1.1.14.000 (AIX, Linux, Windows)
Fixing Level: 8.1.14.100
Brute force attack
An IBM Spectrum Protect storage agent could allow a remote attacker to perform a brute force attack by allowing an unlimited number of login attempts to the storage agent without locking the administrative ID. A remote attacker could exploit this vulnerability using brute force techniques to gain unauthorized administrative access to the IBM Spectrum Protect storage agent and the IBM Spectrum Protect server with which it communicates.
Attack target: information leakage
Existing attack scenarios: Not known
Affected: Spectrum Protect Server up to 8.1.1.14.XXX (AIX, Linux, Windows)
Fixing Level: 8.1.15
IBM Spectrum Protect Operations Center
In some cases, an unsuccessful attempt to log on to IBM Spectrum Protect Operations Center does not result in an increase in the number of invalid administrator logons on IBM Spectrum Protect Server. An attacker could exploit this vulnerability using brute force techniques to gain unauthorized administrative access to the IBM Spectrum Protect server.
Attack target: information leakage
Existing attack scenarios: Not known
Affected: Spectrum Protect Server up to 8.1.1.14.000 (AIX, Linux, Windows)
Fixing Level: 8.1.14.100
User account
While a user account is set up for the IBM Spectrum Protect server, it may be configured to use SESSIONSECURITY=TRANSITIONAL. In this mode, it may be vulnerable to an offline dictionary attack.
Attack target: information leakage
Existing attack scenarios: Not known
Affected: Spectrum Protect Server up to 8.1.1.14.XXX (AIX, Linux, Windows)
Fixing Level: 8.1.15
Spectrum Protect Server, Backup/Archive Client, Space Management and Spectrum Protect for Virtual Environments
An unspecified vulnerability in Java SE related to the JSSE component could allow an unauthenticated attacker to obtain sensitive information, resulting in a high confidentiality compromise, by using unknown attack vectors.
Attack target: information leakage
Existing attack scenarios: Not known
Affected:
Spectrum Protect Client up to 8.1.1.14.0 (AIX (Web User Interface only).
Linux (Web User Interface only), Windows, Macintosh)
Spectrum Protect for Space Management up to 8.1.14.0 (AIX, Linux)
Spectrum Protect for Virtual Environments 8.1.14.0 (Linux, Windows)
Spectrum Protect Server 8.1.14.XXX (AIX, Linux, Windows)
Fixing Level: 8.1.15
An unspecified vulnerability in Java SE related to the JSSE component could allow an unauthenticated attacker to obtain sensitive information, which has a minor impact on confidentiality, by using unknown attack vectors.
Attack target: information leakage
Existing attack scenarios: Not known
Affected:
Spectrum Protect Client up to 8.1.1.14.0 (AIX (Web User Interface only).
Linux (Web User Interface only), Windows, Macintosh)
Spectrum Protect for Space Management up to 8.1.14.0 (AIX, Linux)
Spectrum Protect for Virtual Environments 8.1.14.0 (Linux, Windows)
Spectrum Protect Server 8.1.14.XXX (AIX, Linux, Windows)
Fixing Level: 8.1.15
Backup/Archive Client
OpenSSL is vulnerable to a denial of service caused by a flaw in the BN_mod_sqrt() function when parsing certificates. By using a specially crafted certificate with invalid explicit curve parameters, a remote attacker can exploit this vulnerability to cause an infinite loop, resulting in a denial of service condition.
Attack Target: Denial of Service
Existing attack scenarios: Proof of Concept
Affected: Spectrum Protect Backup-Archive Client up to 8.1.1.14.0 (Linux, Windows)
Fixing Level: 8.1.15
User credentials
IBM Spectrum Protect Client stores user credentials in plain text that can be read by a local user.
Attack target: information readout
Existing attack scenarios: Not known
Affected: Spectrum Protect Backup Archive Client up to 8.1.1.14.0 (AIX, HP-UX, Linux, Macintosh, Solaris, Windows)
Fixing Level: 8.1.15
Denial of service for IBM Spectrum Protect client operations
The IBM Spectrum Protect processes dsmcad, dsmc, and dsmcsvc incorrectly handle certain read operations on TCP/IP sockets. This can result in a denial of service for IBM Spectrum Protect client operations.
Attack Target: Denial of Service
Existing attack scenarios: Not known
Affected: Spectrum Protect backup archive client up to 8.1.1.14.0 (AIX, HP-UX, Linux, Macintosh, Solaris, Windows)
Fixing Level: 8.1.15
If you need assistance with installations or updates, please do not hesitate to contact us.
Your Empalis-Team